As a 1Password admin, there are common audit questions you need to answer around who created various resources. The web dashboard is excellent but some questions are still fiddly to answer. Questions like:
This post is a note-to-self on how to find these answers1.
Who created this group?
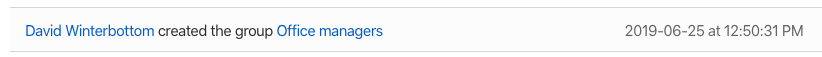
If the group hasn’t had much activity, you can see the creator in the activity timeline section of the group detail page in the web dashboard.
Most of the time though, the creation event will have scrolled off the bottom and won’t be visible:
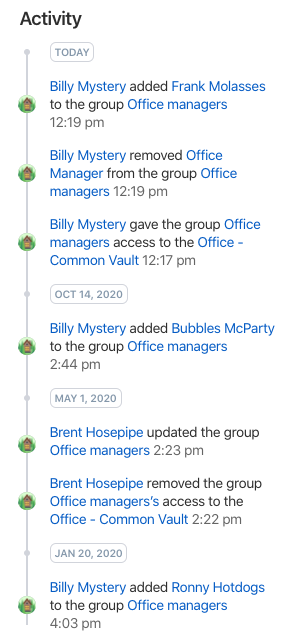
So you need to extract the creation date of the group using the 1Password CLI
tool combined with jq:
$ op group list --format=json | \
jq -r '.[] | select( .name == "$GROUP_NAME" ) | .created_at'
2019-06-25T11:50:31Z
Once you have the creation date, use the “Jump to Date” functionality within the “Activity Log” page (plus a bit of scrolling) to find the creation event record which indicates the group creator.
Pretty fiddly.
Who created this vault?
Like groups, it’s sometimes possible to see the creation event in the timeline section of the vault detail page.
But when that doesn’t work, we can’t use the op CLI tool as the results don’t
include creation dates:
$ op vault list --format=json | jq '.[] | select( .name == "$GROUP_NAME")'
{
"id": "xggkqd3fu2nqndcxsxensdpcxe",
"name": "Some vault",
"content_version": 244
}
Fortunately, the vault creation date is shown in the usage report (which is accessed via a “Create Usage Report” link on the vault detail page):
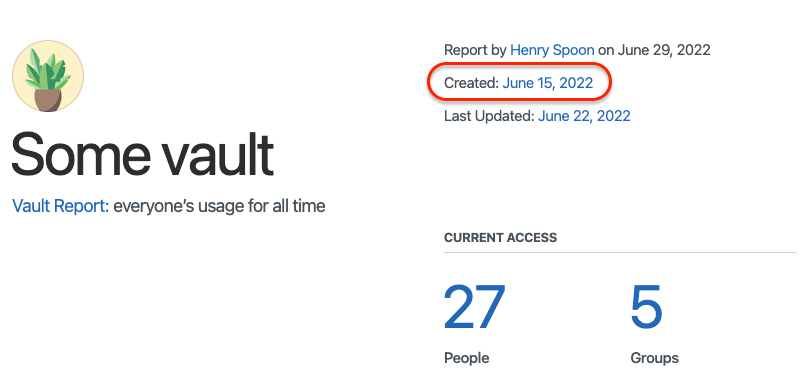
Again we have to use the “Jump to Date” feature of the activity log and scroll around to find the vault creator.

Very labour intensive!
Who created this item?
Open the item’s vault in the web dashboard and select the item.
If the item has never been edited, the creator’s name will be displayed next to the last modified date.
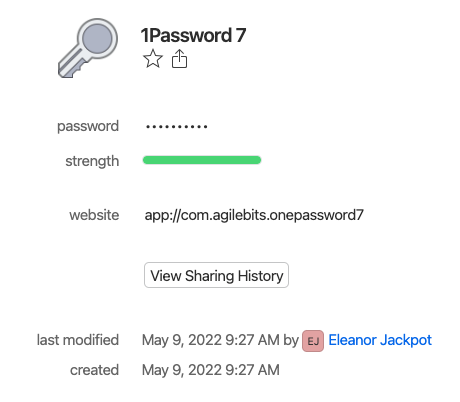
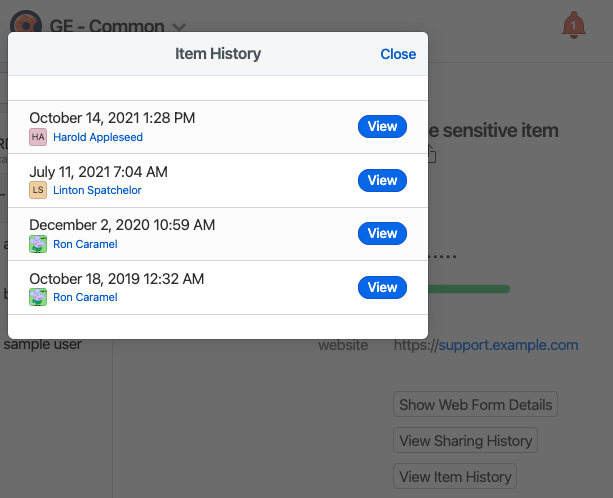
Otherwise use the “View Item History” button and assume the earliest event was creation.
Who has access to this item?
This is tricky. It requires using the op tool to:
- Look up the vault an item belongs to;
- Fetch the users who have direct access to the vault, and those with group access.
- Combined the two sets of users and deduping the two lists of users.
Here’s a Bash script2 that does this.
#!/usr/bin/env bash
#
# Print the users who have access to a given 1Password item.
#
# Note, the `op` tool must be authenticated before this command is run.
set -e
function main {
local item_name="$1"
# Determine the vault ID for the passed item.
local vault_id
vault_id=$(vault_id "$item_name")
# Print the unique emails from the combined lists of direct- and
# group-linked users.
(
vault_direct_user_emails "$vault_id" ;
vault_group_user_emails "$vault_id"
) | sort | uniq
}
# Print the vault ID for the given item name.
function vault_id {
op item get --format=json "$1" | jq -r '.vault.id'
}
# Print a list of user emails who have DIRECT access to a vault.
function vault_direct_user_emails {
op vault user list --format=json "$1" | jq -r '.[].email'
}
# Print a list of user emails who have GROUP access to a vault.
function vault_group_user_emails {
op vault group list --format=json "$1" | jq -r '.[] | .id' | \
while read -r group_id; do
op group user list --format=json "$group_id" | jq -r '.[].email';
done
}
main "$@"
This is harder than it should be
To any 1Password employees, this is harder than it should be. Please consider making these questions easier to answer.
One suggestion: these questions would be easier to answer with more advanced filtering of the activity log in the web dashboard. If we could filter by object UUID then several of the above audit questions could be answered with a single query.
-
Advice accurate as of version 7.9.5 of the macOS, version 2.5.1 of the
opCLI app and the June 2022 version of the 1Password website (revision3211ea83f663according to thedata-gitrevattribute in the page source). ↩︎ -
This version has been simplified a little to fit on the page. Refer to this Gist for an up-to-date version. ↩︎